Retracted Paper "Honeynet Implementation in Cyber Security Attack Prevention with Data Monitoring System Using AI Technique and IoT 4G Networks"due to the ethical issues and plagiarism policy after re-review
DOI:
https://doi.org/10.17762/ijcnis.v14i3.5603Keywords:
Internet of Things (IoT), Cyber Attacks, Cyber Physical System (CPS), Session Key, Artificial Intelligence (AI), HoneyNetAbstract
Cyber Physical Systems (CPS) comprises of the ubiquitous object concept those are connected with Internet to provide ability of data transmission and sensing over network. The smart appliances transmits the data through CPS devices with the implementation of Internet of Things (IoT) exhibits improved performance characteristics with significant advantages such as time savings, reduced cost, higher human comfort and efficient electricity utilization. In the minimal complexity sensor nodes cyber physical system is adopted for the heterogeneous environment for the wireless network connection between clients or hosts. However, the conventional security scheme uses the mechanisms for desktop devices with efficient utilization of resources in the minimal storage space environment, minimal power processing and limited energy backup. This paper proposed a Secure Honeynet key authentication (SHKA) model for security attack prevention through effective data monitoring with IoT 4G communication. The proposed SHKA model uses the lightweight key agreement scheme for authentication to provide security threats and confidentiality issues in CPS applications. With the implementation of SHKA HoneyNet model the data in IoT are monitored for security mechanism in IoT environment. The middleware module in SHKA scheme uses the Raspberry platform to establish internetworking between CPS device to achieve dynamic and scalability. The secure IoT infrastructure comprises of flexible evaluation of user-centric environment evaluation for the effectiveness. The developed SHKA model perform mutual authentication between CPS devices for minimal computation overhead and efficiency. The wireless channel uses the dynamic session key for the secure communication for cyber-attacks security with lightweight security in CPS system. The SHKA model demonstrate the effectiveness based on consideration of three constraints such as low power processing, reduced storage and minimal backup energy. Experimental analysis stated that proposed SHKA scheme provides lightweight end-to-end key establishment in every session. The CPS devices generates the session key of 128 bit long. The minimum key size is implemented to provide effective security in IoT 4G communication with minimal execution time. The simulation results demonstrated that SHKA model exhibits effective cyber-attacks for the constraint devices to improve performance of IoT network.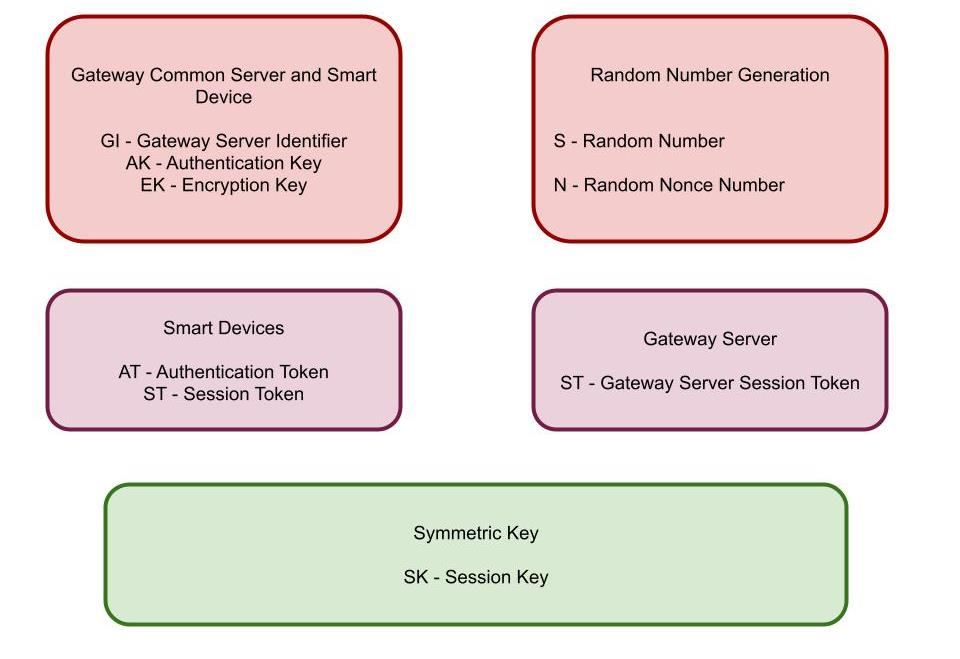
Published
How to Cite
Issue
Section
License
Copyright (c) 2022 Author

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.




