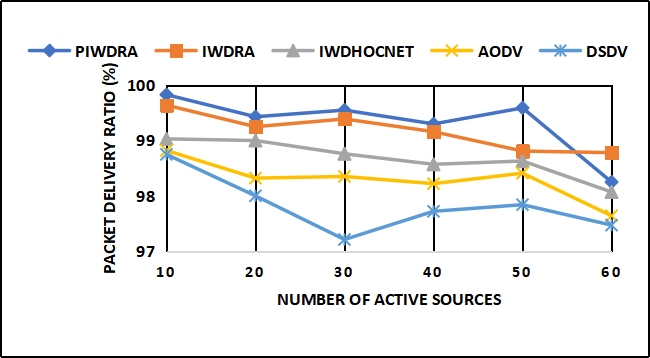
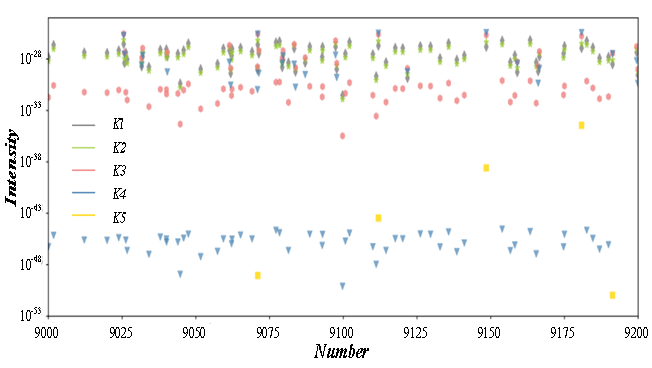
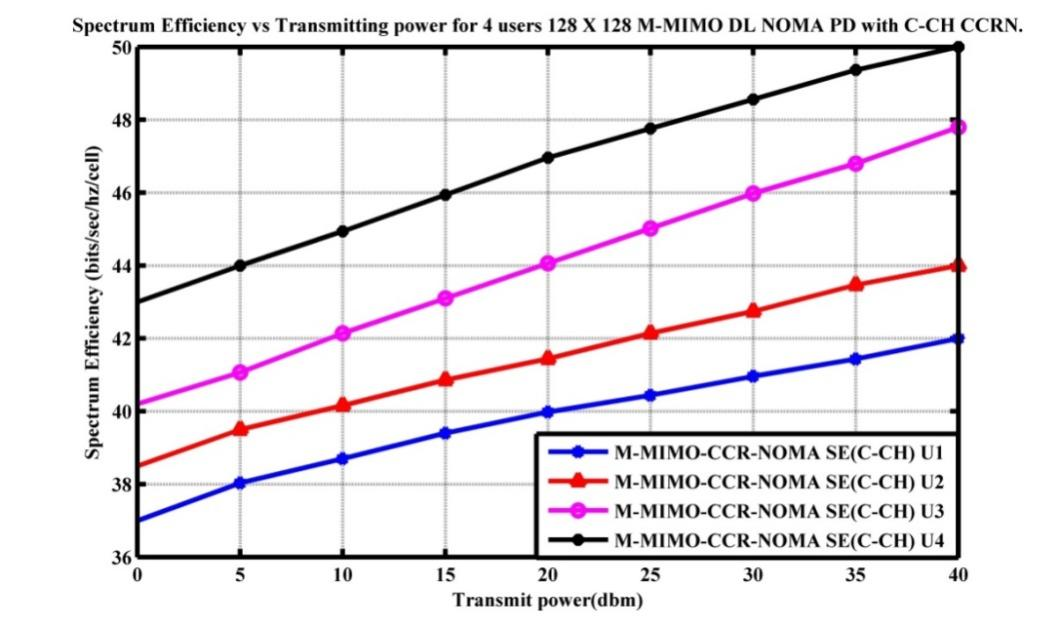
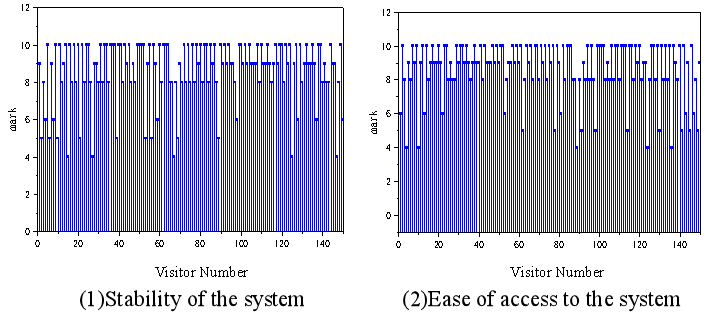
Information
Keywords
International Journal of Communication Networks and Information Security(IJCNIS) is a scholarly peer-reviewed international scientific journal published four times (March, June, September, December) in a year, focusing on theories, methods, and applications in networks and information security. It provides a challenging forum for researchers, industrial professionals, engineers, managers, and policy makers working in the field to contribute and disseminate innovative new work on networks and information security