Generative Boltzmann Adversarial Network in Manet Attack Detection and QOS Enhancement with Latency
DOI:
https://doi.org/10.17762/ijcnis.v14i3.5607Keywords:
Edge computing, Quality of service, Resource estimation, Virtualization, Machine learningAbstract
With the advancement of Internet of Things (IoT), the network devices seem to be raising, and the cloud data centre load also raises; certain delay-sensitive services are not responded to promptly which leads to a reduced quality of service (QoS). The technique of resource estimation could offer the appropriate source for users through analyses of load of resource itself. Thus, the prediction of resource QoS was important to user fulfillment and task allotment in edge computing. This study develops a new manta ray foraging optimization with backpropagation neural network (MRFO-BPNN) model for resource estimation using quality of service (QoS) in the edge computing platform. Primarily, the MRFO-BPNN model makes use of BPNN algorithm for the estimation of resources in edge computing. Besides, the parameters relevant to the BPNN model are adjusted effectually by the use of MRFO algorithm. Moreover, an objective function is derived for the MRFO algorithm for the investigation of load state changes and choosing proper ones. To facilitate the enhanced performance of the MRFO-BPNN model, a widespread experimental analysis is made. The comprehensive comparison study highlighted the excellency of the MRFO-BPNN model.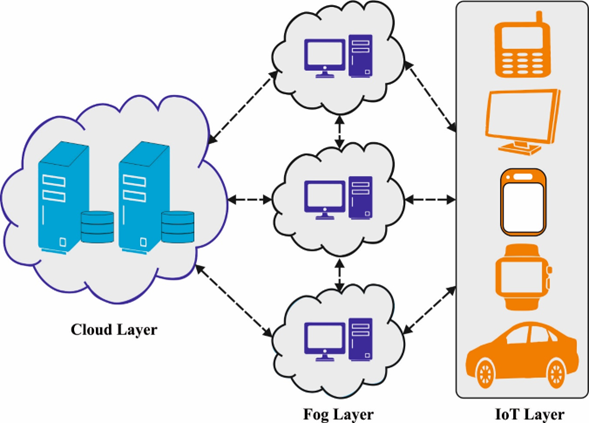
Downloads
Published
Versions
- 2023-01-03 (3)
- 2023-01-03 (2)
- 2022-12-31 (1)
How to Cite
Issue
Section
License
Copyright (c) 2022 Author

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.




