Comparative Analysis of Traditional and Modern Proxy Solutions in Cyber Security
DOI:
https://doi.org/10.17762/ijcnis.v16i2.6689Keywords:
Proxy, Cyber Attack, Secure Web Gateways, Phishing Attack, Cutting-Edge TechnologiesAbstract
This paper presents a broad comparative analysis of traditional and modern proxy solutions in cyber security landscape. This paper is highlighting the effectiveness, applications, and impact of these proxies in different cyber security environments. Through an extensive literature review, this paper explores the evolution of proxy technologies. A thorough evolution is presented here from basic content filtering and caching tools to sophisticated security techniques. And how these security solutions are integrated with advanced features. These features are deep packet inspection (DPI), real-time threat intelligence, and encryption management of traffic. The quantitative and qualitative data from the University of Maryland CISSM Cyber Attacks Database is used to analyze trends, frequency, and financial impacts for different organizations. This analysis is identifying a major increase in proxy-related attacks and highlighting importance of strong proxy solutions required to handle these growing sophisticated attacks. We investigate different case studies, like high profile breaches at OKX, i2VPN, and the 911[.]re. This investigation is showing real-world applications and consequences of proxy attacks. These case studies provide a qualitative input to our understanding. Also, these case studies are highlighting specific methodologies and mitigation strategies being used by the hackers to breach cyber security solutions. Our findings are showing that modern proxy solutions are considerably outperforming the traditional proxies in different parameters of cyber security. Like security effectiveness, scalability, and adaptability are the main parameters where modern proxy solutions are more proactive and more secure as compare to the tradition proxy solutions. This paper determines different lessons learned and recommendations for enhancing security of organizations. This paper concludes by emphasizing the need for continuous monitoring, comprehensive incident response plans, and employee training.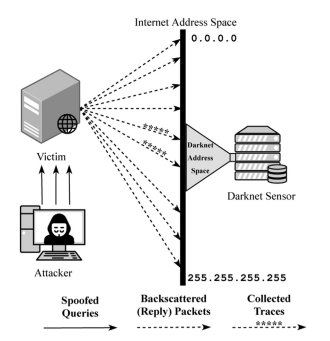
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 International Journal of Communication Networks and Information Security (IJCNIS)

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.





